Ransomware is a very dangerous type of malware. These software perform data encryption. Sometimes will lock the user's device access. They work on both computers and mobile devices. Once successfully installed on the user's device, the hacker will demand a certain amount of ransom to return the device or data access. Through this article, Mat Bao will learn the concept of Ransomware. As well as instructions on how to prevent this scam method.

What is Ransomware? Why is ransomware so dangerous?
Concept
First let's learn about the concept of Ransomware:
Ransomware (or ransomware) is a form of malicious software. It prevents the user from being able to access and use the data inside the server (or computer in general). The attacker will demand a ransom from the victim to restore access to the data. However, the user does not always get the data back when paying at the request of the attacker).
From the above concept, we can see that the ultimate goal of ransomware is money. Often the hacker will ask the victim to pay in virtual currency units or by wire transfer. In the last few years, ransomware spreaders have preferred Bitcoin. Due to the high security of this coin, it is very difficult to trace.
Events that have taken place
First of all, GrandCrab (2018) First appeared in January 2018. This Ransomware has scammed more than 50,000 victims in less than a month. GrandCrab is spread through phishing and malvertising emails. This is the first known malware that has requested ransom payments in the DASH cryptocurrency. Initial ransoms range from $300 to $1500. The malware was eventually destroyed by the Romanian authorities along with Bitdefender and Europol (a free data recovery suite).
In addition, if you are a regular Internet user, you must remember WannaCry (2017). A worldwide cyber attack. This malicious code infected more than 300,000 computers in 4 days. WannaCry is propagated through an exploit channel known as EternalBlue. Microsoft Windows operating systems were targeted (most of the affected computers were running Windows 7). The attack was stopped due to emergency patches released by Microsoft. American security experts claimed that North Korea was responsible for the attack. But no proof was provided.
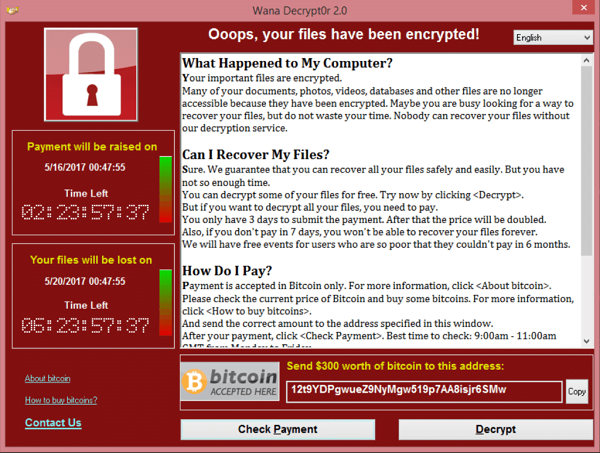
Through the above events, we must have known that the danger of Ransomware. Next, learn how it works.
How Ransomware Intrudes and Works
In general, the operation and use of the Internet always need to be careful in selecting information. Like other forms of Internet fraud / extortion, ransomware spreads due to the carelessness of users:
- Find and use cracked, unlicensed, unknown software.
- Clicking on or opening malicious files or links attached to e-mails
- Clicking on ads containing ransomware
- Accessing websites containing depraved, unhealthy content embedded with malicious code.
However, the most typical and common is still through email. When a user opens an email attachment, malicious code is installed on the victim's computer. In addition, hackers can also embed malicious code into the website. When users visit these websites, malicious code will be installed on the system.
Users are often unaware of the malicious code's infiltration process. Because they often run in the background of the system (background). When the data locking mechanism is activated, a dialog box appears informing the user that the data has been locked/encrypted. As well as asking for a ransom to unlock/decrypt the data.
What to do when infected with ransomware & Remedies
Should you pay when infected with Ransomware?
Careless when using the Internet can lead to being infected with ransomware. When detecting a device infected with Ransomware, we should not pay ransom because:
- Data recovery cannot be guaranteed even after ransom is paid. For example: There are often bugs in malicious code that make encrypted files unrecoverable. Even with the decryption key.
- If we pay the ransom it will prove that the malicious code works. At that time, the hacker will continue to perform actions to find new methods. From there exploit the system, encrypt data and demand ransom.
- Some ransomware already have a decryption tool (Decryption Tool). We can use these tools to decrypt, recover locked or encrypted data.
Effective Ransomware Handling Measures
Many security organizations and law enforcement agencies have built many projects to support users with tools and programs to recover encrypted data. These are tools that help us determine what kind of ransomware has been infected with a computer. And from there is there a corresponding tool to decode or not. Can refer to:
The following, Eye of the storm will guide users how to use No More Ransom to handle when the device is infected with ransomware.
Handling ransomware with No More Ransom
To determine the type of ransomware your computer has been infected with, perform the following steps:
- Step 1: Visit 's website address No More Ransom
- Step 2: Do the following:
– Upload 02 encrypted files in box 1. Note that the file size is not larger than 1MB
– Enter the correct email address, website URL and/or bitcoin address in the ransom pop-up. Or upload a file (.txt or .html format) containing the hacker's ransom content into box 2.

- Step 3: Choose GO! FIND OUT to start the process of finding and determining the type of ransomware and the corresponding decryption tool (if any).
- Step 4: Search results will have 2 cases:
– Case 1: Found the type of malicious code and the corresponding encryption data decryption tool. Read the instructions carefully before downloading the tool and follow the instructions carefully
– Case 2: No ransomware and corresponding decryption tool found:
Note: Not all types of ransomware have a decryption tool. However, in this case, we should back up the encrypted data to wait for a solution, a decryption tool for this type of malicious code in the future.
Prevention and conclusion
In general, Ransomware is still an obsession of Internet users. Most of today's malicious code has a corresponding decryption tool, but there are still a few Malware that have not found a decryption tool. That's why "prevention is better than cure" is the most important thing. To prevent Ransomware that is evolving daily on the Internet, users should take the following recommendations:
Back up your data regularly, install and update anti-virus software.
Use trusted Anti-virus software such as Symantec, Sophos, Norton, McAfee or Windows Defender to protect your computer system from ransomware. Regularly update to the latest version and do not turn off the "heuristic" function of Anti-virus software to ensure the detection of the latest, undetected ransomware.
Avoid clicking on links or e-mails when you don't know what they are.
Beware of strange links or files: On the internet, any account can be hacked and malicious links can be sent from these accounts via social media or e-mail. .
Never open files or attachments in e-mails from people we don't know. Hackers often distribute fake e-mails to trick users into clicking, then malicious code will be installed on computers. This is a very common form of attack. Therefore, the awareness of users to protect themselves from malicious attacks is very important.
Source: Eye of Storm synthetic
WARNING: Ransomware and its prevention first appeared on Tech Support Center | MATBAO.NET.







Post a Comment
Post a Comment